I finally completed the migration of my DNS records for my instance of Gitea (hosted on my raspberry pi). After Comcast maintenance resulted in changing my IP address and breaking my DNS records, I began to move services to Cloudflare using Tunnels.
I'm frustrated that their documentation still largely refers to using cloudflared to set up tunnels but when you do so you are told that this method will no longer be supported and that you should use the web dashboard instead.
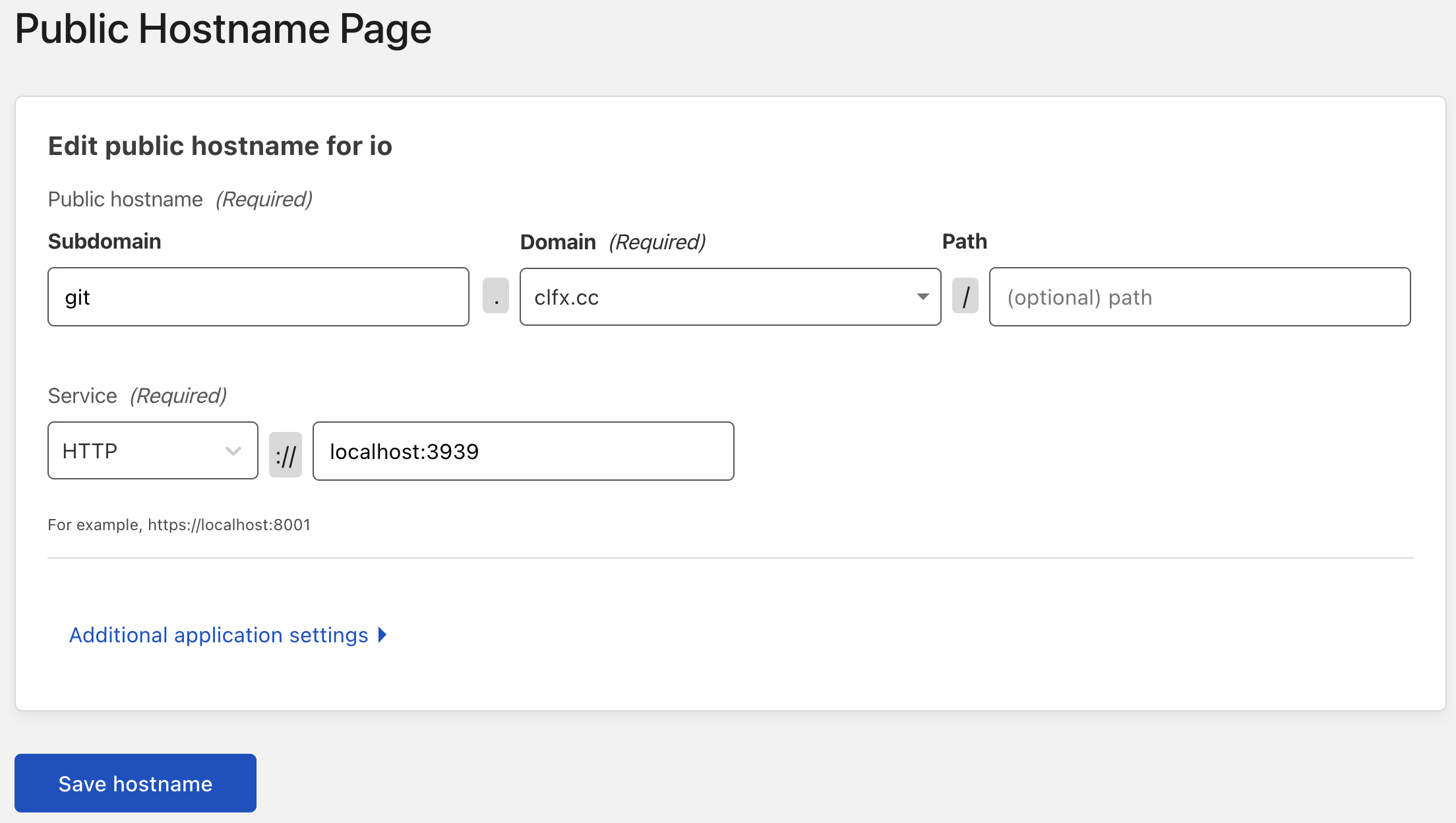
Fair enough, I ended up doing exactly that and did find the process to be relatively painless for forwarding all of my HTTP traffic.
No longer will I have to manage the renewal of SSL certificates (which I had automated but in an unreliable way), and I could benefit from DDOS protection as well as Cloudflare's CDN.
Besides content caching being a little annoying when I have an underlying file updated, I'm absolutely loving the benefits of securing my applications through what I believe Cloudflare once called "Argo Tunnels" (I don't see this name in the new UI).
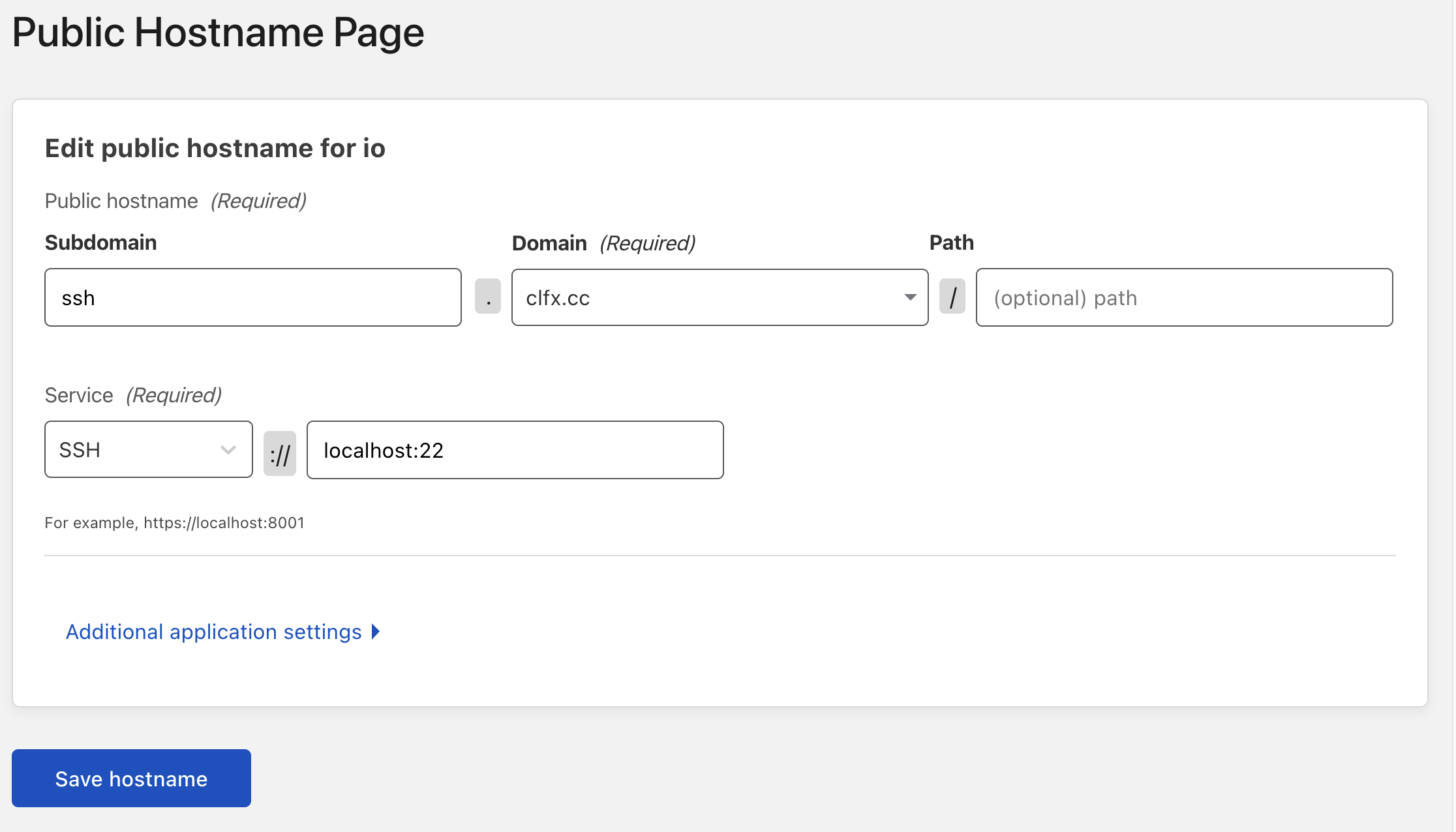
The only problem I encountered during my migration was getting SSH tunneling to work.
After coming back to it about a week later, I eventually realized it was because the type of traffic (TCP) was not HTTP, Cloudflare was handling it differently and wanted me to ssh in a different manner.
I had a lot of trouble finding the right documentation on this subject but eventually came across this forum post which contained the critical clue.
I needed to create an ssh configuration in ~/.ssh/config that would use a different command (not ssh) to proxy the traffic correctly.
Later I found this official documentation
First I needed to install cloudflared on my machine, which happens to be an M1 mac, meaning I needed to use my arm64-based brew (installed to /opt/brew) to install it.
For some reason my machine still defaults to reporting itself as an x86 shell so I have the following aliases defined in ~/.bash_aliases to let me switch between the shells:
alias arm64='env /usr/bin/arch -arm64 /bin/bash --login'
alias x86='env /usr/bin/arch -x86_64 /bin/bash --login'
So after running arm64, I am able to successfully run the installation command:
brew install cloudflared
With the necessary application installed and in my PATH already, I added the following lines to ~/.ssh/config:
Host git.clfx.cc
Hostname ssh.clfx.cc
ProxyCommand cloudflared access ssh --hostname %h
User git
AddKeysToAgent yes
IdentityFile ~/.ssh/id_rsa
This way my git repositories could still use git.clfx.cc as their remote URL but under the hood we are actually connecting to ssh.clfx.cc by way of cloudflared. So much more secure than before (which required me opening up port 22 on an IP address listed publicly via DNS).
In Cloudflare's Zero Trust Dashboard, under "Access > Tunnels", I had to configure the HTTP and SSH "Public Hostname" connection with the fields I had presumed would work originally:


and then was able to git clone / push / etc to my Gitea instance using both SSH and HTTP remote-urls.
I tried and failed to get .htaccess files configured in a way that would allow me to have descriptions for my files.
But I did find out it was possible to customize the HTML and all of those things that the index page has.
Some basic CSS would go a long way.
Maybe this is the kind of thing I should look to fiverr for.